One, drone security incident
To date, the drone industry has become the fastest growing consumer electronics industry in addition to mobile phones, computers, and wearable devices. More and more ordinary consumers also have more opportunities to reach areas and institutions that can't be reached by normal channels through drones.
In addition, in addition to civilian and consumer-class drones and aircraft, special unmanned aerial vehicles for more specialized and special applications are becoming new applications. such as:
Faster, more powerful flying motors, FPV competitive drones, fastest speeds up to 150KM/h to 200KM/h. Some military ultra-high speed UAVs are 700 to 1000 KM/h.
Larger load capacity, can reach more than 20KG professional drone. Fixed-point delivery can also be supported. Military drones can reach a load of 1 ton.
Longer battery life, larger batteries can support up to 30 minutes to 1 hour of life. Military drones can achieve up to 40 hours of battery life.
With a larger range of maneuverability, the current maximum range for special purpose drones can often reach 2,000 to 5,000 kilometers, and military drones can even reach 18,000 kilometers.
More complex task prefabrication, integrated face recognition technology, custom dynamic target locking and tracking technology, and preset functions such as tasks and routes all make the drone capable of performing tasks that are more intelligent and independent.
With all-weather drones, more and more drones have all-weather flight capability to adapt to day, night, weather and weather conditions.
Air-to-air amphibious drones currently have IP67 waterproof drones for use in fishing, rescue, scientific research, and extreme sports. Can land or take off from the water, and even observe the situation below the surface of the preset position and the real-time picture.
Miniature and hidden drones, currently the smallest drone is only the size of a coin. The SQ4 Recon developed by the British military can continuously fly or hover for 30 minutes in the air, and can be parked on a building to avoid surveillance. It can perform an 8-hour continuous investigation. The United States has also developed a "fly" with a size of only 106 grams and the size of a coin. The flight does not fly through the common rotor, but it is a bionic flap. It is also more sensitive to complete the more difficult flight through the wings.
More professional audio and video real-time broadcasting, in addition to commonly used WIFI or analog audio and video transmission channels, military and special-purpose UAVs also use more professional satellite audio and video communication technology can achieve long-distance audio and video data acquisition and dissemination.
Advanced data acquisition, in addition to audio and video, more sensors bring more data acquisition options, such as climate, temperature, humidity, altitude, terrain, coordinates, precision mapping, infrared imaging, laser ranging, remote sensing telemetry.
For different application scenarios, these special unmanned aerial vehicles all play their respective strengths. Military drones are used in battlefield and enemy intelligence gathering. At present, some of the targets for civilian special-purpose drones have reached or even exceeded military use. If these drones are used in some illegal espionage, more or destructive criminal activities. All may cause irreparable loss of people’s property and national interests.
Threatening national security
On the evening of February 24, 2015, five UAVs of unknown origin hovered over the US Consulate in Paris. Even if the French police mobilized the police, the drones flew over the Eiffel Tower and the Place de la Concorde.
Threatening politicians' security
On September 15, 2013, German Chancellor Angela Merkel had a drone crashed in front of multiple chief officials and Merkel himself before a campaign rally. There was no warning before this.
In April 2015, a drone carrying radioactive material crashed at the residence of the Japanese Prime Minister.
On June 30, 2013, the South African police arrested a man outside Pretoria Hospital, where former President Nelson Mandela was resident, when the man was using a remote-controlled helicopter model to photograph the hospital.
Between 1995 and 2014, there were a total of 100 terrorist attacks on explosives, chemical or biological weapons carried out by drones targeting political figures around the world, of which only 16 were able to be cracked.
Threatening military bases and important infrastructure security
In November 2014, more than 20 drones intensively flew over a number of nuclear facilities in France.
At the end of 2014, after a destroyed nuclear reactor in Belgium was reopened, it was visited by a micro-drone next day.
On January 28, 2015, some light drones flew near the anchorage of the BREST military harbor. The anchorage site is a French nuclear military base and there are four nuclear submarines capable of launching submarine-launched nuclear missiles.
Threatening the security of important secrecy units
On January 26, 2015, a drone crashed into the no-fly zone of the White House and crashed into the area. During this process, the air defense radar system did not find the whereabouts of the aircraft.
On August 14, 2015, a drone crashed near the HMP Pentonville prison in England. The police intercepted a large quantity of drugs and mobile phones they carried. Local* have found that drones are being used more and more for the smuggling of contraband items in prisons in England and Wales.
Threatening people's public safety
In December 2013, an avionics company employee in Beijing manipulated illegal drone surveys near the Capital Airport, resulting in delays in the evacuation of multiple civil aviation aircraft.
In the second half of 2014 alone, the U.S.A.A. FAA recorded 175 incidents of approaching or impacting civilian airliners by drones.
In 2014, the FAA survey conducted by the United States Aviation Administration revealed that in large-scale outdoor sports events, incidents of unauthorized drones and crashes often occurred, as many as nearly a thousand.
Used for illegal activities
On January 22, 2015, a UAV at the Mexican border crashed due to overload. It attempted to transport drugs and weapons. Such incidents frequently occurred in the region.
In a local election in Afghanistan in March 2015, extremist groups used drones to disperse leaflets of extreme thoughts, inciting voters' hearts and affecting the election results.
Threatening communication information security
Former U.S.* members Mike Tassey and Rich Perkins succeeded in DIY an unmanned reconnaissance plane. This unmanned reconnaissance plane can carry out WI-FI password cracking, telephone tapping, and SMS interception.
The above examples are just a few typical examples of many public security threats. However, today's drones we face are far more vulnerable than ever. We cannot simply and recklessly ban drones from the territory of our country. After all, such high-tech products have brought a lot of positive influence on our lives. Therefore, seeking an effective management approach is the correct solution.
Second, the UAV defense technology analysis
The UAV defense technology is basically divided into detection, identification, and domestication. According to the different requirements of users, defense schemes are also designed to different levels of effectiveness and defense. The existing mainstream UAV identification technologies are mainly realized through several methods of radar, audio monitoring, and video monitoring. And a simple technology has its own shortcomings:
Radar detection technology: The smallest UAV target that can be detected and identified can detect targets in the range of 0.006 square meters to 0.01 square meters. However, the difficulty lies in the fact that many objects such as birds, kites, balloons, and gas-phase observing devices are used for objects of similar size. How to accurately identify the UAV based on the reflected echo requires system software to be able to store as many characteristic echoes as possible. Make further accurate judgments. Another difficulty for the radar system is that there are more noise sources in the low-altitude area, which is a great degree of interference for the final judgment. In the drone defense solution of Shenzhen Xiaozhuang Technology, there are several types of radar devices in the radar equipment section that can be selected to suit different applications, including long-range radar, boundary radar, and mobile radar detection and interference integration system. According to the characteristics of the target site we have a tailor-made solution.
Audio detection technology: The current audio detection technology is based on sound waves generated by a UAV or aircraft motor vibration generated by a fixed frequency range. Generally, the range of detection varies with the degree of environmental noise. The detection range in mountainous or rural areas will be relatively large, while the detection distance in urban areas will be relatively close. At present, the most advanced audio detection equipment can detect the range within a range of 1 km in the mountain environment. The biggest difficulty in audio detection technology is the detection sensitivity and accuracy of the ambient noise in the urban environment. In addition, the drones with different power modes have different frequency responses due to the characteristic noise generated by the flight. For example, the noise spectrum generated by the quadrotors and the eight rotors, battery power, and fuel power are all different. Without a complete database of characteristic noise, it is difficult to accurately determine the existence of all drones. In Shenzhen Xiaozhuang’s UAV defense program, audio detection technology, which is an auxiliary method for radar detection, is also used in the detection of UAVs, especially for some radar signals that are difficult to cover due to radar signal boundary regions and buildings. In the area, audio detection is able to compensate for the lack of radar detection, so that "no dead ends, no omissions" of the probe. Its audio detection sensors include omnidirectional concealable professional microphones and long-distance high-sensitivity stereo parabolic microphones. The entire device can be easily installed and used to hide the host part. There is also a powerful feature noise frequency response database that subdivides the drones, power sources, and volume of drones. System operation is more reliable.
Composite imaging monitoring technology (high-definition video, infrared imaging, thermal imaging, laser detection and measurement): The traditional video monitoring methods can only be used after the target detection, with different imaging such as high-definition video, infrared imaging, thermal imaging, etc. The technology and the central control software visually judge the target. The combination of measurable images and GPS/IMU fusion technology can track the target trajectory and the target's 3D model, which all provide strong support for the later analysis. However, the difficulty lies in the fact that its use alone is affected by weather and environmental factors, and it does not work well in harsh wind and rain conditions such as wind, rain, and fog. The use of a site in a wide area does not work well. In the drone defense scheme of Shenzhen Xiaozhuang Technology, video surveillance is only used as a part of the entire detection and identification system and plays a role in auxiliary judgment. All video surveillance probes (HD video, infrared imaging, thermal imaging, laser detection and measurement) along with boundary radars and jamming systems are all integrated on the integrated head. Form a three-dimensional detection, identification, tracking, domestication defense system.
Radio Frequency Interference: After completing the steps of UAV detection and identification, it interferes with its RF control signals, forcing the UAV to land without returning. It will not cause further information leakage or greater safety hazards. These follow-up actions are particularly important. . The current drone interference scheme mainly involves interference with GPS, GSNS, GLONASS, Beidou and other positioning signals, WIFI, WIMAX, and wireless control signals of fixed frequency bands, as well as audio and video transmission signals for interference, covering HF, VHF, UHF, SHF. , Cellular Networks, Satellite Phones, GPS and other frequency bands. Causes the controller to lose control of the drone and continue to fly. In the drone defense solution of Shenzhen Xiaozhuang Technology, there are different types and configurations of RF jammers for different applications and sizes. There are fixed equipment jammers assembled with video surveillance and boundary radars. Mostly suitable for fixed-point assembly applications; there are applications integrating radar and jamming systems in on-board applications, with strong mobility, mostly used in * and large-scale assembly activities, etc.; also available for low-cost RF interference with limited budget The gun, after finding the intruding target, artificially targets the target within a limited distance to interfere with its control and positioning signals.
Other aids: Measures applied to drone defense and other auxiliary measures, such as the detection of illegal drone operators, the use of directional sound cannons to remotely warn the intruder to stop illegal activities, or stop the flight command. . A strong sense of discomfort will force persistent dissuasive operators to lose control of drones. In addition, in addition to radio-frequency jamming guns, some backpack-type RF jammers interfere with wireless signals in specific bands within a more effective range. Shenzhen Xiaozhuang Technology also provides similar technical solutions.
Third, conventional defense case
High-risk infrastructure defenses, such as prisons, nuclear power stations, or highly classified sites. For the important infrastructure, high-confidentiality and high security requirements of the unit organizations, the recommended equipment in the Shenzhen Xiao Zhuang Science and Technology drone defense program are: boundary radar, audio detectors, composite video surveillance (selected use), radio frequency interference system. According to the size of the defensive zone, the number of installations and the location of the installation need to be planned accordingly. The following is a plan for installing a nuclear power plant project.
In this design solution, each installation point includes a remote control head, boundary radar, audio detector, and radio frequency interference system. Complex video surveillance systems, long-range monitoring radars, etc. can be selected based on project budget due to cost and practicality. At the same time, field security personnel also recommend the use of handheld radio frequency interference guns, which are inexpensive, flexible, and easy to use, and can assist in the domestication of illegal drones.

No-fly zone, military base. In the same scheme, boundary radars, audio detectors, and radio frequency jammers are also used as the main equipment to form a closed defense barrier at the periphery of the defense area. It is possible to use a border radar with a wider range of power and a wider range of sound detectors. Early discovery can allow more time for interference domestication. If funds permit, you can consider installing long-range radar at the center of the site, which can cover targets within a radius of 4.5 kilometers.

Large-scale assembly activities in stadiums, plazas, and densely populated areas. In this application scenario, the defense system needs to be quickly and temporarily constructed. The system solution requires features such as high accuracy, strong mobility, repeated use, and simple system setup. In Shenzhen Xiaozhuang's drone defense solution, a dedicated vehicle-borne radar monitoring and RF interference integration system can be applied to this application. Sites or buildings with relatively concentrated crowds of people within a short period of time are quickly parked in designated locations by a fast-moving onboard system. The number of vehicles and systems depends on the area of ​​the defense area. When the assembly or activity is completed, the system can be quickly revoked and can be used again and again at another site.
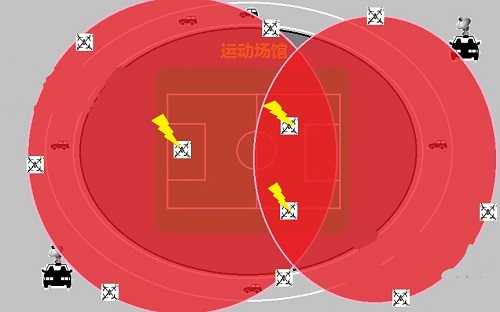
Temporarily define no-fly zones, such as emergency situations. For the application needs of violence or rapid emergency response, there is also a high requirement for the convenience and speed of defense system construction. It is recommended to use a dedicated vehicle-borne radar monitoring and radio frequency interference integration system, and in the case of ample budget, you can consider the installation of long Radar, within a radius of 4.5 km.
The low-cost defense scheme, if the cost is very limited, generally suggests that the user only considers the radar detection part, and the function of the radio frequency interference can be provided by the security personnel with a radio frequency jamming gun or other low-cost drone trapping scheme.
Shenzhen Xiao Zhuang Science and Technology drone defense solution mainly provides customized solutions for different application occasions and scale user requirements. There is no "10 000 essential oil" type drone defense scheme, and a scheme suitable for a certain occasion does not equally satisfy another application requirement. The focus of different users' attention will also be different, as well as some common problems such as boundary detection capabilities, building shadowing areas, domestication of drones, correct discrimination in the same area*, and illegal drones. Therefore, Xiaozhuang Technology focuses on customized drone defense solutions.
Panda Car,Geely Automobile Mini Car,Geely Mini Cute Bear Car,Panda Mini Cute Bear Car
Xi'an Luguang Xincheng Trading Co., Ltd , https://www.lgxc-autosales.com
